How to Secure Your Hazelcast Cloud Deployments
Securing your data is much more critical than ever before, as security breaches and cyber attacks continue to escalate. Security is a must, but generally, it requires tradeoffs in performance and user-friendliness. With Hazelcast Cloud, we provide you with several ways to secure your deployments without losing the performance and simplicity of Hazelcast.
Hazelcast Cloud leverages Hazelcast Enterprise, which has a very comprehensive security suite that enables you to secure your data in different layers and in different ways. In this article, I will explain the options and when you can enable them.
1- Cluster Credentials
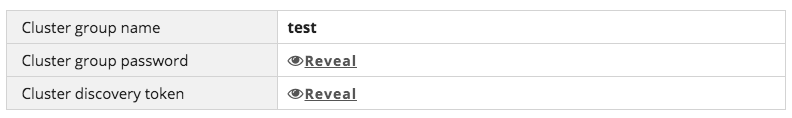
This is the basic and default level of security in Hazelcast Cloud. Hazelcast Cloud generates a strong password for each cluster as well as a discovery token. The client code uses the token to find and connect to the right cluster, and the password helps with the authentication. So this means that if someone figures out your cluster’s password and discovery token, he/she can easily connect to your cluster with full privileges. That’s why you should keep the password secret but also consider enabling other security options. I will explain these options below in addition to basic security, especially for your production clusters. In the cluster dashboard, when you click the “Configure Client” button, you will see the credentials for the cluster as below:
2- Encryption in Transit – TLS
Hazelcast Cloud allows you to encrypt socket-level communication between the Hazelcast cluster and Hazelcast clients for end-to-end encryption. TLS is important for providing privacy and data integrity between the Hazelcast cluster and clients. We strongly recommend enabling TLS for your production deployments in the cloud.
How to Configure
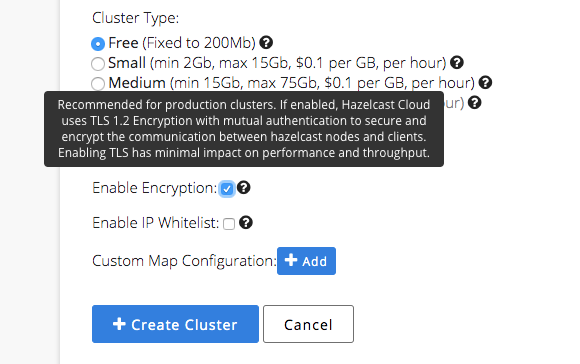
As shown above, you can enable TLS while creating a Hazelcast cluster. Once enabled, you need to configure your clients accordingly. Fortunately, you can download a preconfigured sample client and use it as a boilerplate. For more about client configuration, review this page.
Note that you cannot disable TLS on a running cluster; you need to create a new one and terminate the older one.
Mutual Authentication
Hazelcast Cloud has two-way authentication, which means both client and cluster authenticate each other. Both client and cluster should have TLS keys, so that any client without the key store file cannot authenticate to the cluster. This helps to secure your cluster against any attacker who managed to obtain your cluster’s IP address and credentials.
Performance Overhead
In general, TLS/SSL can have a significant impact on performance. Hazelcast Cloud uses OpenSSL together with optimizations to minimize the performance overhead. You can expect about 10% degradation in throughput, but this is quite small when compared to similar products (e.g., Redis with TLS).
3- IP Whitelisting
While Hazelcast credentials and TLS (mutual authentication) provide authentication on the application level, IP whitelisting does it on the network level. When you enable IP whitelisting, your cluster will accept connections only from the IP addresses in the whitelist. In other words, your cluster is only accessible by a set of clients with specific IP addresses.
How to Configure
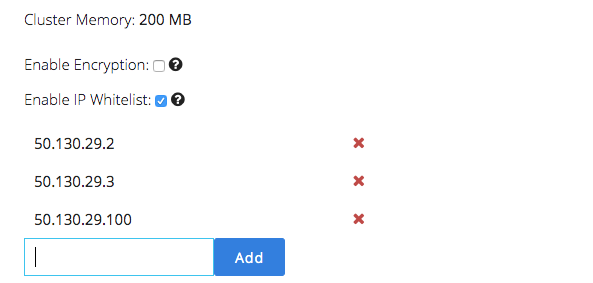
As you can see above, you can enable it in the cluster creation step, but you can also enable IP whitelisting on a running cluster, as shown below. You can add/remove IP addresses and the changes go into effect instantly.

Note that your clients should have static IP addresses. If your client’s IP changes, it cannot reconnect to the cluster in case of a disconnection.
4- Role-Based Access Control
The options above are for the authentication of Hazelcast clusters, while role-based access concerns the authorization of users of Hazelcast Cloud. In the dashboard, you can create teams and invite users. Team clusters will be accessible by team members with respect to their roles. The following roles are available:
1- View Only: This role can only view the charts and metrics but cannot create, stop, or update the clusters.
2- Developer: This role can update the cluster in addition to seeing the charts and metrics, but it cannot update and access payment settings and team settings.
3- Admin: This role has access to everything, including payment and team settings.
4- Finance: This role only has access to payment setting and billing information.
If you are working as a team, it is recommended to assign teams and users with correct roles. Also, it is good practice to create different teams for development and production clusters. That way, you can give restricted privileges to most people for the production cluster, while clusters in the development team will be accessible and updateable by many.
How to Configure
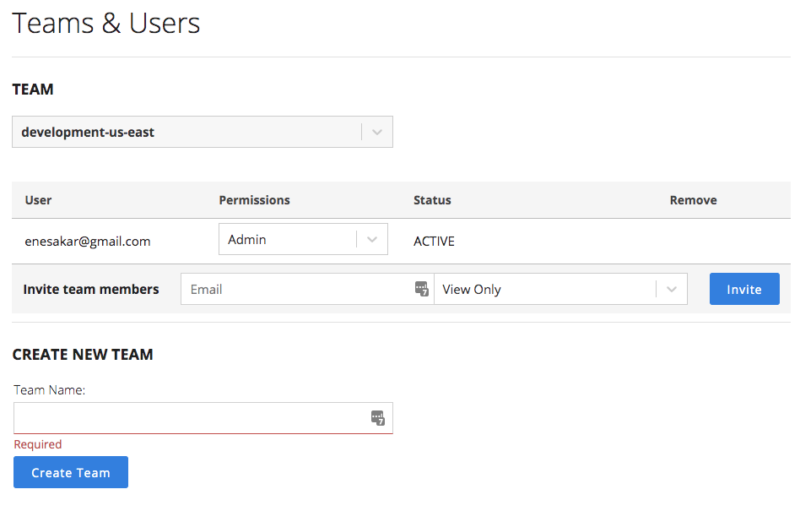
As shown above, you can create teams on the dashboard using the menu “Account > Team & Users.” Once you create a team, you need to switch to this team to create clusters specific to this team. Switching the team is via the combo box on the right top corner of the dashboard.
What About VPC?
VPC (Virtual Private Cloud) enables users to run their applications in networks that are isolated in the cloud. VPC is probably the best way to secure your cloud deployments. Note that we couldn’t leverage VPC in Hazelcast Cloud because of the Hazelcast Cloud multi-tenant nature. However, in our next edition (Hazelcast Cloud Dedicated), each cluster will work on a VPC dedicated to a specific cloud user.
