Hazelcast LDAP Security


Hazelcast has the ability to authenticate users of a cluster and then to authorise their access to data structures and operations based on roles held by a user. This authentication and authorization occurs within the cluster when a client connects for the first time.
Introduction to Hazelcast & JAAS
The entire process is handled with the help of JAAS (Java Authentication and Authorization Service) compliant interfaces.
The follow three steps describe at a high level how Hazelcast interacts with JAAS. The highlighted words denote keywords in the JAAS lexicon.
- The Subject(Hazelcast Client) attempts to connect to a service, in this case a Hazelcast Cluster. The Subject provides Credentials when it initially connects. These Credentials can be anything at all, for example a user name and password or maybe a Binary Token.
- The Credentials are passed to a LoginModule, this module is a JAAS interface that is executed by the Hazelcast Cluster when a new client connects. The implementer of this module may then take the passed Credentials and firstly authenticate the user. The authentication can be carried out against the security service of their choice. This could just be a Database table of user names and password or it could be a corporate security solution like LDAP or Active Directory.
- Once the user has been authenticated they can then be authorized to perform actions on data or execute distributed functions. This authorization takes the form of matching roles against actions in Hazelcast, for example “Joe Bloggs” has the role of “Admin” therefore he can update all Maps in the cluster. The roles are generally stored in the same security back-end/database that carried out the Authentication steps, maybe an LDAP or Active Directory store.
The following diagram describes these operations.
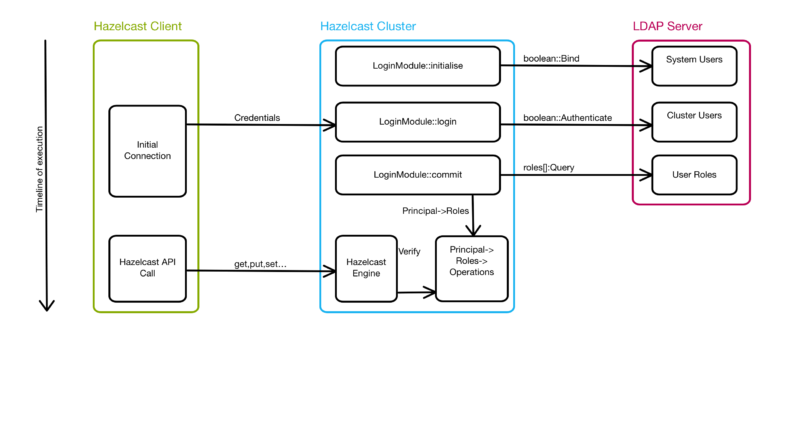
JAAS Login Module Phases
If you examine the diagram above, within the Hazelcast Cluster each member will have a LoginModule registered to it (we’ll look at how we register the module later on), The LoginModule is an interface defined in the JAAS specification. It is this interface we need to implement to provide a link between Hazelcast Client connections and our Security back-end.
Now observe the lifecycle phases of the LoginModule, in the diagram above we can see initialise, login & commit. There are a couple of others we need to be aware of that handle failed login attempts and also logout.
Here’s the JAAS LoginModule interface in its entirety.
javax.security.auth.spi.LoginModule.java
